Originally published by The IoT Magazine on 9/24/2018
Gartner estimates that there are over 8 billion connected Internet of Things (IoT) devices and nearly two-thirds of consumers are worried about how their gadgets could be compromised. Consumers and vendors should be worried!
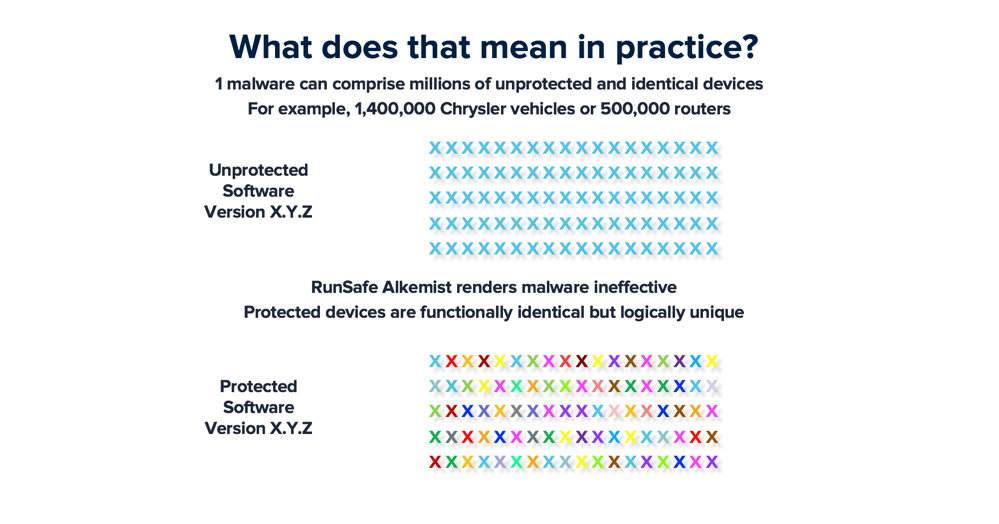
Personal privacy and security have already been compromised by previously innocuous, but now internet-connected gadgets from spying teddy bears to spying robot vacuum cleaners. Vulnerabilities present in millions of identical devices have already been used to take down the Internet itself and have the potential to do so for the electric grid as well.
Issues with traditional detection
So, what can suppliers and manufacturers do for existing and new devices? Organizations traditionally bolted on cyber detection solutions for data centers and PCs in hardware, software, and services — — firewalls, Intrusion Detection Systems (IDS), and antiviruses. They then had to engage specialized staff to feed and care for those new systems.
These types of solutions are unlikely to work well for the universe of IoT devices because the environments are so different:
- Power and performance IoT devices may not be powerful enough to allow the addition of new components, with retrofitting difficult or impossible for older devices,
- Cost Competitive market pricing tied to Bills of Materials (BoM) may not be able to support additional hardware, software, and services components on devices,
- Time and resources Existing resources are focused on User Experience (UX), features, and speed to market rather than the entirely different skillsets of cybersecurity engineering and monitoring, and
- Supply chain control Suppliers and manufacturers are unlikely to control third party software and hardware for existing or new builds, which may contain invisible malware.
Solution of protecting software images themselves
Suppliers and manufacturers do control the software image that is deployed on existing and new devices. We already know that the detection approach does a poor job with data centers and PCs — more security monitoring and after-action reporting than protection.
What if we focused on protecting software images directly rather than simply trying to anticipate any and all possible future attacks? The independent organization MITRE publishes a top 25 list of issues in software, the CWE (Common Weakness Enumeration) list. In the IoT context, attacks cluster around just a few vectors — overflows, authentication, and encryption issues.
Virgil Security and RunSafe Security can protect images against these key attack vectors in approach called “Signed and Stirred.” The fictional spy “007” was very particular about what ingredients went into his signature martini and also how it was prepared. We feel the same way, focusing on effective protection tools and making them easy and quick to deploy correctly, for example in code signing with Virgil and binary stirring with RunSafe.
A classic mistake by integrators, government and enterprise customers is having a good set of tools but making subtle mistakes in their implementation, thereby leaving vulnerabilities still in place.
- Virgil Security SDK - Prevents authentication-based attacks - Prevents encryption-based attacks
- RunSafe Alkemist binary transformation - Prevents scaling from a single device to all identical devices - Prevents fileless attacks — Memory corruption (buffer overflow, stack, and heap) attacks — ROP/JOP execution re-ordering (Return/Jump Oriented Programming) - Prevents compromised supply chain attacks
Unfortunately, there is no such thing as a magic bullet, so if IoT devices have design-level flaws, neither RunSafe nor Virgil can help. What they can do is massively reduce attack surfaces and prevent scaling attacks for DDoS (Distributed Denial of Service) and ransomware, without requiring rip and replace solutions.
How does Virgil work?
Data security is one of the most critical aspects of IoT devices, which transmit and receive large amounts of sensitive data. The three core pillars of data security are confidentiality, authentication and integrity. We’ll address all three using end-to-end encryption and digital signing.
The concepts of authentication and encryption are relatively straightforward. You want to make sure that the data coming to and from a device cannot be read by or changed by anyone except the allowed parties (not even PubNub, the database, ISP, etc.) and you want to ensure that the IoT device and anything communicating with it is who they say they are.
This is your system without end-to-end encryption. Every component in your backend has access to every single bit of data submitted to your backend services. No secrets. No privacy.
And this is what it will look like after you implement client-side end-to-end encryption:
The messages are encrypted on the IoT device and remain encrypted as they travel over the network/Wi-Fi/Internet, through the cloud/web server, into the database, and on to their final recipient.
Virgil Security’s PubNub SDK makes this easy to build. The primary functions are as follows:
- Create and publish users’ public keys on Virgil Cards Service.
- Encrypt data with a receiver’s public key before sending.
- Decrypt encrypted data with a sender’s private key after receiving.
- Create tamper proof signature to be sure of data integrity.
This method of encrypting and signing data secures the data communications between an IoT device (confidentiality), ensures that only the proper parties are interacting (authentication) and ensures the data has not been tampered with (integrity).
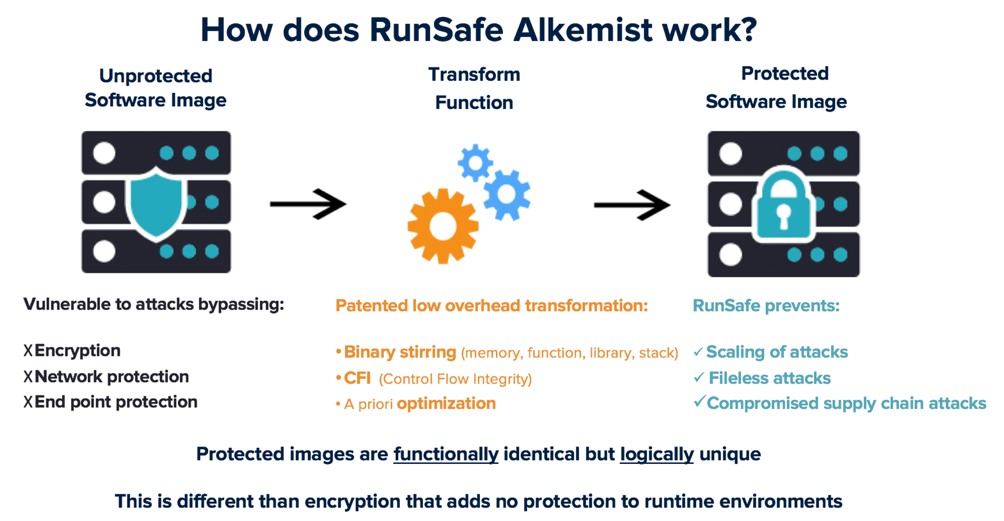
How does RunSafe Alkemist work?
RunSafe’s Alkemist prevents scaling attacks, fileless attacks, and compromised supply chain attacks. Since it cuts down whole attack surfaces, it is well positioned to stop zero-days that depend on them. The Alkemist transformation can easily be applied to existing and new systems, with no special skills, or on-going requirements around monitoring.
The current software image is replaced with an Alkemist transformed version that fits back into the same hardware footprint — Figures 1 and 2. The transformation leverages patented binary stirring of memory, functions, libraries, and the stack; Control Flow Integrity (CFI); and apriori optimization techniques, with minimal performance, or sizing overhead.
These techniques have some superficial resemblances to legacy and known ineffective ASLR (Address Space Layout Randomization), DEP (Data Execution Protection), and NX (No execute) bit approaches but are not the same.
Figure 1 Transformation of binaries
Figure 2 Functionally identical but logically unique binaries
Virgil Security
Virgil Security, Inc., makes every software developer into an applied cryptologist. Virgil provides password-free authentication, encryption, distributed immutable data storage via Blockchain, and verification of data, devices, and identities that is quickly and easily integrated into developer products — often in just hours — with no prior cryptographic knowledge or training required. Virgil provides this via a cloud-based service in combination with open sourced libraries that are available for desktop, embedded (IoT), mobile, and cloud / web applications with support for a wide variety of modern programming languages.
Learn more at VirgilSecurity.com and follow us on Twitter at @VirgilSecurity.
RunSafe Security
RunSafe Security is the pioneer of a patented cyberhardening transformation process designed to disrupt attackers and protect vulnerable embedded systems and devices. With the ability to make each device functionally identical but logically unique, RunSafe Security renders threats inert by eliminating attack vectors, significantly reducing vulnerabilities, and denying malware the uniformity required to propagate. Headquartered in McLean, Virginia, with an office in Huntsville, Alabama, RunSafe Security’s customers span the critical infrastructure, IIoT, automotive, medical, and national security industries.
Read more at www.runsafesecurity.com, and follow us at @RunSafeSecurity.