By Alexey Ermishkin, Chief Product Security Officer at Virgil Security, Inc. and co-author of the NoiseSocket protocol
Telegram recently announced Telegram Passport, a new service that allows users to upload and store documents such as their passport, drivers license, and bank statements and then share them with third party services, such as ICOs, crypto wallets, and anyone complying with Know Your Customer (KYC) regulations, that desire to verify the user’s identity.
First we must give Telegram full credit for publishing their API as open source. Their commitment to openness gives security practitioners the opportunity to review their implementation and, ideally, help improve it.
Unfortunately Passport’s security disappoints in several key ways.
The biggest concern is around password protection. Passwords are the underlying data protection mechanism in the Passport product. Telegram states that “Your identity documents and personal data will be stored in the Telegram cloud using End-to-End Encryption,” but they’re using SHA-512, a hashing algorithm that is not meant for hashing passwords. LivingSocial learned this in 2013 after they lost 50 million passwords hashed with SHA-1, as did LinkedIn in 2012 when they lost 8 million passwords hashed with SHA-1. And, in the case of LinkedIn, 90% of the hashed passwords were reversed within a week.
Protecting passwords with SHA-512, even if salted, leaves passwords – and their users – vulnerable to brute force attacks.
Using the Telegram desktop client code, let’s take a look at how Telegram’s Passport service actually works and enumerate some of our security concerns along the way:
- You encrypt your data “with a password that only you know.”
- You upload this data to the Telegram cloud.
- When you need to authenticate on a third party service, you decrypt that data and re-encrypt it for that service’s credentials.
Step One: Encrypt your data with a password
With Passport, the only protection user has is his password. Telegram does not use digital signatures, which means that if a user’s data is tampered with, no one will notice including himself. So the password and its security are of the utmost importance.
Here’s the code that turns a user’s password into an intermediate encryption key:
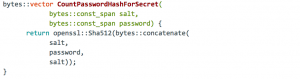
The password is concatenated twice with a random salt and put into a hash function called SHA-512. It seems okay at first, but you know what? It’s 2018 and one top-level GPU can brute-force check about 1.5 billion SHA-512 hashes per second. That means that ten such GPUs (a small cryptocurrency mining farm) can check each and every 8 char password from a 94 char alphabet in 4.7 days! That’s $135/password in the worst-case scenario, using US average electricity costs for the calculation. In practice though, this number can go down to $5/password or even less, given people’s choices of password complexity.
There are many ways to make the life of brute-forcers harder. Using password-hardening techniques such as SCrypt, BCrypt, or Argon2 will slow down the password-hacking process. But Telegram chose not to use these techniques even though there are abundant cautionary tales for those who don’t - like LivingSocial and LinkedIn.
Still, password-hardening algorithms are a step in the right direction. But while they do require extra computational resources, they do not completely prevent brute force attacks; they just make them more expensive. New, stronger technology exists for those who really care about password security, like Virgil Security’s implementation of Pythia for breach-proof passwords and BrainKey for password protected data that cannot be cracked offline or by using brute force.
Step Two: Generate your data encryption key
Let’s move on to the next piece of code created by the Telegram team. This code generates an “almost” random key for data encryption which is later encrypted by the intermediate key we got above:
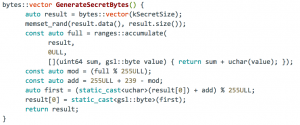
We’re calling it “almost” random because it adjusts the first byte of random byte array in a way that the sum of all bytes is 0 mod 239. Telegram seems to have invented their own way of verifying that those secret bytes were decrypted properly. It’s unclear as to why they didn’t use HMAC or AEAD cipher. Also, it turns out this speeds up the potential brute-force because calculating a byte sum is much much faster than HMAC.
Step Three: Encrypt your data and upload it to the cloud
Next up is the primary data encryption method. Let’s break it down.
This piece of code adds between 32 and 255 random bytes to the plaintext data that is being encrypted in order to make it look more random-ish.
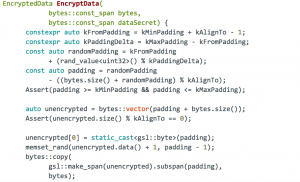
Here, the “almost” random key is concatenated with data hash, put into another SHA-512 invocation and used for data encryption.
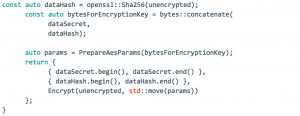
Intermediate result:
Telegram cloud receives the following data parts:
- Plaintext+random bytes data hash
- “Almost” random key encrypted with password using SHA-512
- Salt
- Encrypted data
Brute force attack
All this allows an attacker with access to the user password hash table (be they internal or external attackers) to perform brute-force attacks very efficiently with the following algorithm:
- Take the next password and calculate SHA-512 using salt (GPU)
- Try to decrypt the intermediate key (AES-NI)
- Calculate sum of all the bytes and discard all cases when sum mod 239 != 0
- Calculate data decryption key candidate using another SHA-512 call (GPU)
- Try to decrypt the first block and check its first padding byte which will be enough in many cases
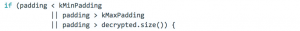
Conclusion
Cryptography’s most famous anonymous quote says “Don’t roll your own crypto!” Back in 2015, Telegram ran into similar criticism. In 2016, 15 million Telegram users' phone numbers were revealed in Iran due to a user authentication flaw. Now it’s 2018 and with Telegram’s Passport, the quote has never been more true.
The security of the data you upload to Telegram’s Cloud overwhelmingly relies on the strength of your password since brute force attacks are easy with the hashing algorithm chosen. And the absence of digital signature allows your data to be modified without you or the recipient being able to tell.
There are additional concerning techniques: generating an encryption key from one SHA-512 call, embedding a checksum inside an encryption key, using plaintext for generating a data encryption key, etc.
Given the sensitivity and value of the documents being stored – passports, drivers licenses, financial statements, rental agreements, and more – Passport will be a high value target for attackers. That Telegram again “rolled their own crypto” and failed to implement a secure solution for this high profile product is alarming and it opens the door for attacks from both within and without.
True End-to-End Encryption
End-to-end encryption has become a marketing feature and that is a double-edged sword. Now, when people see “end-to-end encrypted,” they believe that their data will safely be sent to a third party without worries of it being decrypted or tampered with. Unfortunately, Passport users will have a false sense of confidence about the security and privacy of their data as it can be breached due to the weakness of Passport’s password security.
What are the alternatives?
The good news is that there are proper end-to-end encrypted solutions with well-tested cryptography implementations and protocols that have been approved worldwide.
Virgil Security provides one of them. Virgil is the technology behind Twilio’s End-to-End Encrypted messaging and we’re used in healthcare, financial, and crypto applications worldwide to protect user data, passwords, and more.
In addition to our free open source SDKs that allow developers to build End-to-End Encrypted products & applications, we offer Pythia: a breach-proof password solution and BrainKey, which creates complex keys from simple passwords, and together stop brute-force and offline attacks on passwords while using cryptography protocols and mathematics reviewed by cryptographers, security practitioners, and scientists.
--
Virgil Security, Inc. makes every software developer a cryptographic expert. With Virgil Security, every developer can quickly and easily build cryptographic features such as encryption, password-free authentication, immutable data storage via Blockchain, and cryptographic verification of data, devices, and identities, into their products, with no cryptographic training, often in just minutes. Virgil’s open-source libraries are available for desktop, embedded (IoT), mobile, cloud, and web applications in a wide variety of modern programming languages. Founded in 2014, Virgil Security is headquartered in Manassas, Virginia, USA, with offices in San Francisco, California, and Kiev, Ukraine. To learn more about Virgil Security, please visit https://VirgilSecurity.com/.
